Home »
Cryptography
Rail Fence Cipher in Cryptography
Cryptography | Rail Fence Cipher: In this tutorial, we will briefly study the basic Rail Fence cipher and examples aim to capture. We will cover types of messages in Rail Fence cipher.
By Monika Sharma Last updated : May 24, 2023
What is Rail Fence Cipher in Cryptography?
In Rail Fence Cipher, given a plain-text message and a numeric key then cipher/decipher the given text using the Rail Fence algorithm.
The rail fence cipher is also called a "zigzag cipher" because we make a rectangle box and write plain text into it in a zigzag form. It is a form of transposition cipher that jumbles up the order of the letters of a message using a basic algorithm. It derives its name from how it is encrypted.
The rail fence cipher works by writing your plain text or message on alternate lines across the prail and then reading off each line or rows in turn by turn.
Rail Fence Cipher Encryption
In a transposition cipher, the order of the alphabets is mixed up or we can say rearrange to obtain the cipher-text or encrypted text.
- In the rail fence cipher, the plain-text is written as zigzag way as firstly go downward till the box is not end and diagonally on successive rails of an imaginary fence.
- When we reach the bottom rail, we simply traverse opposite moving diagonally, after reaching the top rail or top line, the direction is changed again. Thus the alphabets of the plain text are written in a zig-zag form.
- When all the alphabet is fill in the rail then the individual's rows are combined together to give a ciphertext.
Example
The plaintext we have i.e "defend the east wall" having a key size or the size of the row is 3, we get the encryption method below,

That at the end of the message we have inserted two "X"s. These are called nulls and act as placeholders. We do this to make the text fit into the rail so that there is the same number of letters on the top row as well as on the bottom row. Otherwise, it is not necessary, it makes the decryption process a bit easier if the text has this format.
And the cipher text became: "dnetleedheswlxftaax".
Rail Fence Cipher Decryption
As we have studied earlier, the number of columns in rail fence cipher remains equal to the length of plain-text which we took. And the key remains the same as in encryption to the number of rails.
- Hence, the Rail Fence matrix can be constructed likely. Once we have got the matrix we can find-out the places where plain texts should be placed using the same way as we doe in the encryption method of moving diagonally up and down alternatively to form text.
- Then, we fill the cipher-text accordingly to row-wise. After filling the text, we traverse the matrix in the zig-zag form to get the original text or the plain text.
Example
If we get the ciphertext "TEKOOHRACIRMNREATANFTETYTGHH", it will be encrypted with a key size of 4.
We start by placing the "T" in the first square. You then dash the diagonal down places until you get back to the top line, and place the "E" here. Continuing to fill the rows you get the pattern below,

As we have a key size of 4 and the length of the message is 28 so we make like this and continues this till all the text does not fit into it.

Second stage in decryption process,
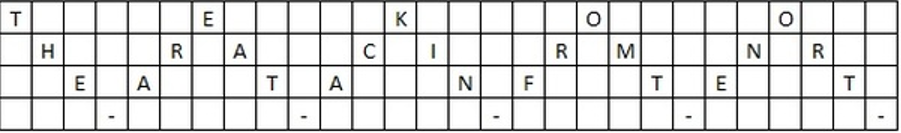
Third stage in decryption process,

Forth and the final stage in decrption process,
Now, we read them as diagonally from top to bottom then bottom to top and we get the plain text or the original text i.e. "THEY ARE ATTACKING FROM THE NORTH".
Reference: Rail Fence Cipher
Advertisement
Advertisement