Home »
Network Security Tutorial
Network Security Architectures - Security Zones (DMZ, Trusted/Untrusted Zones)
By IncludeHelp Last updated : July 27, 2024
What are Security Zones?
Security zones are defined areas within a network with specific security policies and access controls. These zones help manage and reduce risks by separating different types of traffic and resources.
Types of Security Zones
There are three types of security zones in network security, namely: Trusted Zones, Untrusted Zones, and DMZ (Demilitarized Zone).
1. Trusted Zones
A trusted zone is a network segment where the resources and users are considered secure. This zone typically includes internal systems, databases, and employee workstations.
Example
Suppose in your company's internal network, employees access company resources such as email servers, file storage, and internal applications. Since only verified users can access these resources, this part of the network is considered a trusted zone.
Security Measures
- Access Controls: Only legit users can access resources within the trusted zone.
- Firewalls: Firewalls control incoming and outgoing traffic, which ensures only authorised communication.
- Encryption: Sensitive data is encrypted to protect it from unauthorised access.
2. Untrusted Zones
An untrusted zone comprises external networks that we can’t control and may be dangerous. This zone typically includes the internet and any external networks.
Example
When users access your company's website or services from the internet, they are operating from an untrusted zone. Since the internet is open and accessible to anyone, it is considered untrusted.
Security Measures
- Firewalls: Strong firewall rules are established to filter incoming and outgoing traffic.
- Intrusion Detection Systems (IDS): IDS monitors network traffic for suspicious activity.
- VPNs: Virtual Private Networks (VPNs) are used to secure connections between untrusted and trusted zones.
3. DMZ (Demilitarized Zone)
A DMZ is a buffer zone between the trusted internal network and the untrusted external network. It hosts services that need to be accessible from the internet while keeping the internal network secure.
Example
Your company hosts a web server that customers can access to purchase products. This web server is placed in the DMZ. If a hacker takes over the web server, they still cannot access the internal network directly.
Security Measures
- Dual Firewalls: One firewall between the untrusted zone and the DMZ, and another between the DMZ and the trusted zone.
- Limited Access: Only essential services are allowed to operate in the DMZ.
- Monitoring: Continuous monitoring for any signs of intrusion or malicious activity.
Practical Implementation
- Firstly, plan your network with three main parts: trusted zone, untrusted zone, and DMZ.
- Next set up two firewalls: one between the untrusted zone and DMZ, and another between the DMZ and trusted zone.
- Then, place public servers like websites and email servers in the DMZ.
- Ensure strict rules for firewalls and access to manage traffic between these zones.
- Lastly, use tools to monitor the DMZ for any unusual activities.
Real-world Example
Let's consider an online retail business:
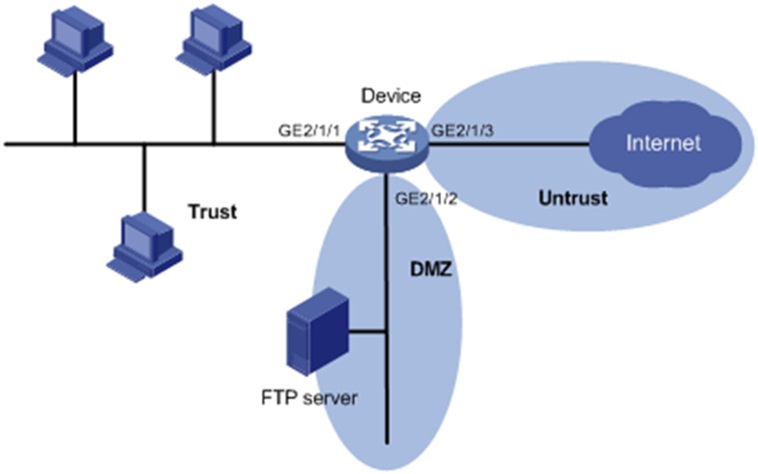
Untrusted Zone: The internet, where customers browse the website.
DMZ: The web server hosting the company's online store, accessible to customers.
Trusted Zone: Internal network with databases storing customer information, accessible only to authenticated employees.
By placing the web server in the DMZ, the company ensures that even if the web server is hacked, attackers cannot directly access sensitive customer information stored in the trusted zone.
Advertisement
Advertisement